QC threatens to render current cryptographic protocols obsolete, forcing the scientific society to research new cryptographic algorithms and security products that are resistant against quantum attacks.
An EY CEO Imperative Study from 2021 shows that QC was not priority for executives over the next two years, representing how the technology is still not ready for everyday commercial applications. However, in a separate survey of UK businesses from 2022, most respondents said their firm will be taking concrete steps to prepare for QC within one to two years. And cryptography is a key area of focus: 72% of the survey’s respondents in technology, media and telecommunications say cryptography-related tasks are their top priority for QC use, while 61% in advanced manufacturing and other fields of industrial production say the same. The consumer, energy and private equity sectors also ranked cryptography as their second-highest priority within QC.
Why CSOs should care about quantum computing today
Although the technology is not yet fully established, today’s data is still vulnerable to QC decryption, as the useful life of data may be longer than the time required to break current encryption methods. This is often referred to as “harvest now, decrypt later” attacks, where bad actors collect encrypted information now in hopes that QCs will be able to crack that encryption in the future. The recent EY Quantum Approach to Cybersecurity report found the following security products are at a high level of risk due to advances in quantum computers:
Public key infrastructure |
Certification Authority (CA), SSL Certificates commonly used. Since 2014, nearly all commercial CAs use RSA public keys of at least 2048 which is considered to be breakable. |
Secure software distribution |
Mostly public key-based digital signatures, containing RSA public keys. |
Federated authorization |
Single-sign-on methods such as OAuth, OpenID and SAML, among others, are widely based on HTTP and once hacked are extremely vulnerable to data theft and criminal acts. |
Key exchange over public channel |
Key-sharing only between individuals Key exchange and key agreement methods are used in network security protocols like SSHE, IKE, IPsec SSL and TLS to protect private communication. They rely to a large extent on RSA, elliptic curve cryptography or Diffie-Hellman (ECDH) algorithms. |
Secure email |
Secure emails commonly sent via S/MIME for predominantly government entities and regulated enterprises to exchange confidential/authentic email. They largely rely on RSA public keys. |
Virtual private network |
IPSec ensures company network access, work-related application access and mobile workforce. VPNs can also be used to circumvent local internet restrictions in foreign countries, creating a tunnelling network enabled via RSA or ECC with key establishment protocols such as IKE or mobile IKE. |
Secure web browsing |
Secure-lock web browsing via SSL/TLS enabled websites, mostly required by regulatory requirements and compliance due to user’s private information, such as payment data. RSA is still the most common authentication key. |
Controller devices |
In-built cryptography of controller devices in any kind of machinery (cars, airplanes, manufactory, etc.) usually don’t have the storage, computing or communication capabilities to support cryptographic methods such as lattice-based ones, and they are often quite difficult to replace. |
Private blockchain transactions |
Blockchain protection algorithms include RSA and ECDSA, thus the crypto world must overcome factoring problem algorithms in order to remain secure. Blockchain transaction signatures for identification and blockchain nodes with internet communication are extremely vulnerable. |
Chief Security Officers (CSOs) can already be formulating a QC strategy that includes:
- Assessing the risks: how much of your encrypted data is at risk?
- Analyzing possible impacts: what would the impact be on your business if this encrypted information was cracked in the next 5-10 years?
- Planning a roadmap: from their current corporate cybersecurity ecosystem to a quantum-powered one — how do we get there from here?
While new QC algorithms will allow businesses to increase their level of security with the inclusion of quantum-resistant cryptography, the security level will also depend on the level of cybersecurity maturity and controls currently in place within the business and the progression of technology in tandem with regulation.
To keep operating successfully and securely, businesses will need to ensure that their quantum-powered cybersecurity plan is fully matured before the threat posed by QC technologies becomes a reality.
To assess the quantum readiness in your cybersecurity business landscape, ask:
- Are data security and encryption essential for your business?
- How well-prepared is your cybersecurity business landscape?
- Are you aware of the cybersecurity threats posed by emerging quantum technology?
- Do you have a full awareness of the risks and threats posed by these technologies?
- Do you have a well-prepared, quantum-powered business model at hand, ready for implementation?
- Are your security protocols “crypto-agile?"
- Can you afford to have sensitive information stolen today to be decrypted when quantum computing technologies are available in the future?
An important step for businesses on the journey toward quantum-resistant cryptography is also to become aware of developments in the regulatory environment. Regulatory efforts to address post-quantum cryptography have begun. In the US, the National Institute of Standards and Technology (NIST) is working on a set of standards, as is the European Telecommunications Standards Institute. NIST standards are expected to be published in 2024.
The three paths toward a quantum-resistant future
Given the threats and regulatory response, the time to act is now. With the following quantum readiness roadmap, entities can assess how ready their cyber business model is for the quantum era and reduce their exposure to quantum attacks. Once the assessment has been performed, the governance model and body can be revised and redefined on the path to a quantum-resilient future.
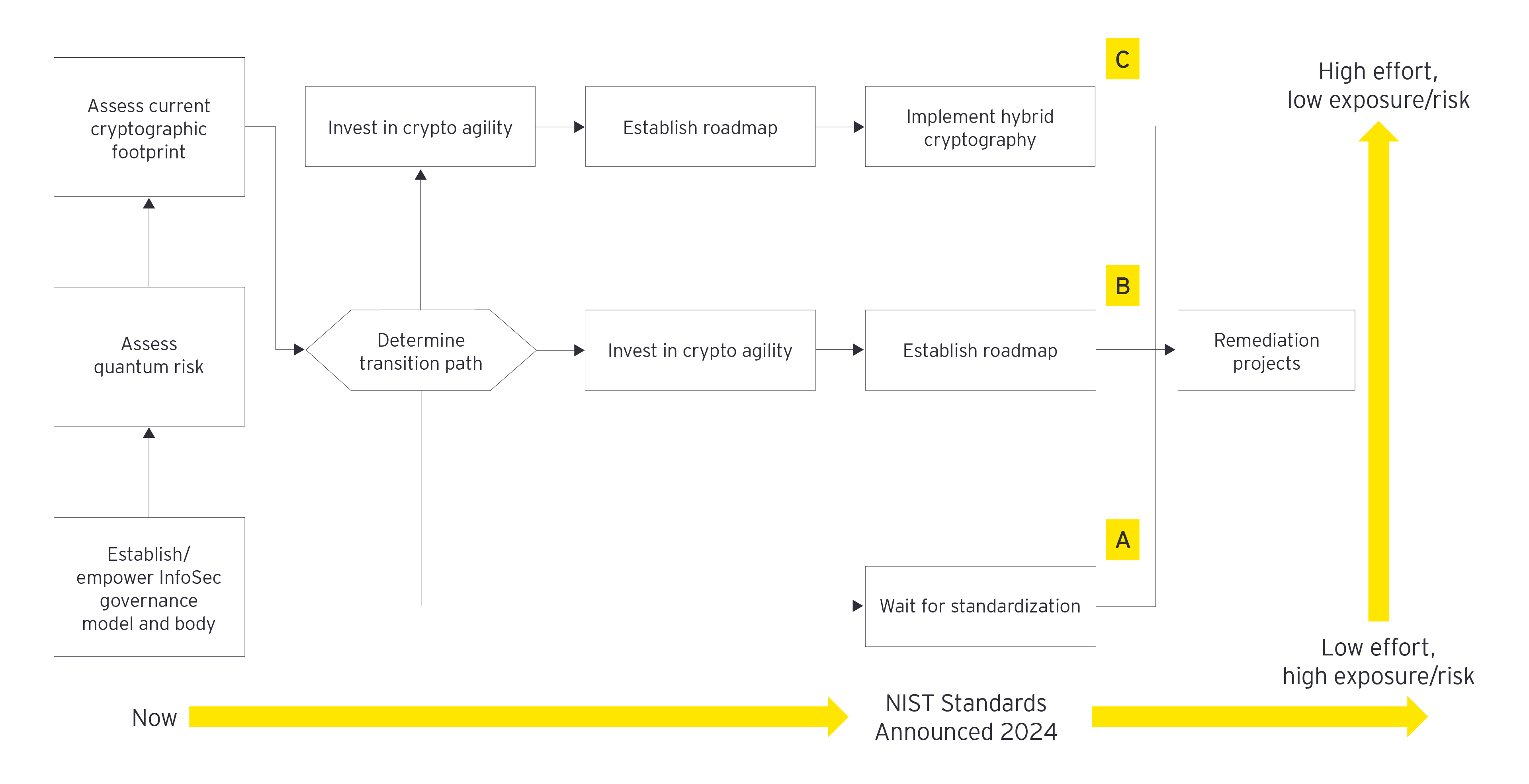
An organization’s readiness for quantum threats and standardization can be divided into three different strategies and scenarios to be applied after a thorough quantum risk assessment, according to the Cybersecurity Research Lab at Toronto Metropolitan University’s Ted Rogers School of Management. Those three, reflected in the above chart, are:
A. Certain organizations will wait for standardization regulations to enter into force before taking any initiative. This includes companies whose data is of relatively low value for potential hackers or data that exists for a short period of time.
B. Some organizations will invest in crypto agility beforehand and be ready to launch appropriate initiatives by the time official standards enter into force by establishing an adaptable and maintained roadmap.
C. Few organizations with higher risk and sufficient resources will go beyond; in addition to being crypto-agile, they will adopt a hybrid posture by implementing a quantum-resistant security layer on top of the existing one. This will help reduce the risk of data being stolen now and decrypted in the future, when fully operational quantum computers will be available for use.
Related articles
Summary
As we move into a quantum-powered future, assessing and reducing your organization’s quantum risk exposure will become paramount. While quantum technology is still in its infancy, the businesses that plan now for a quantum-resilient future will be the ones that can offer the best defense against emerging cyberattack vectors.


